How to Enable IMAP Access to Exchange Mailboxes
Why use IMAP?
At first glance enabling IMAP on your Exchange Server might seem like a backwards step since much of the advanced client functionality that Exchange supports requires a MAPI enabled PIM application, usually Outlook.
However, there are a number of scenarios when using an MS Exchange compatible client is not an option, or cannot provide the functionality you require, e.g.:
- Users with non-Windows systems, such as Macs or Linux based desktops – Although Microsoft's official advice when using Outlook is not an option is to use Outlook Web Access instead, this is not always possible or practical. One obvious drawback of OWA is that it requires a constant connection to the server, which may not be available for a remote Macbook user. Ideally, you want your Mac users to use Entourage, but if this isn't an option then you should consider IMAP.
- Outlook 2011 on Mac with Exchange 2003 – The new Outlook For Mac 2011 cannot connect to Exchange 2003 as it uses Exchange Web Services, only introduced in Exchange 2007. The only option is to enable IMAP and synchronise the mailbox that way instead.
- Mobile devices without Exchange Activesync support – Whilst Exchange support is virtually a prerequisite for any "business class" smartphone nowadays, there are still many devices which don't support it but do offer IMAP access.
- Mobile access to multiple Exchange mailboxes – Virtually all mobile clients (with the notable exception of Apple's IOS4) will only sync with one mailbox, so users cannot check other shared mailboxes without reconfiguring their device each time.
What is IMAP?
Internet Message Access Protocol has been around since 1986, but has rapidly increased in popularity in recent years with the spread of "always-on" broadband Internet connections, replacing POP3 as the preferred protocol for email applications. The main reason for this is that it supports both online and offline modes, unlike POP3 which is purely offline, making IMAP much better for keeping a local client synchronised with a server mailbox. It also supports multiple clients accessing a single shared mailbox, whereas POP3 only allows one connection at any one time.
By default IMAP uses port 143, unless you wish to use SSL encryption in which case it uses port 993. Exchange does allow you to set a custom port of your own choosing if you require. Either way, you need to make sure you open the necessary ports on your firewall so that remote clients can connect to your Exchange Server.
IMAP over SSL
As has just been mentioned, you can use SSL encryption with IMAP to increase security, and you should seriously consider this option if you are supporting mobile clients. IMAP by itself is not a secure protocol so the username and password are transmitted across the network in plain text, making it possible to detect them using a packet sniffer – a particular risk if you have users who may connect from public access points. Chances are that you will have already setup SSL for OWA on your Exchange Server, in which case you can use the same certificate, but if not you will have to obtain one. This isn't the place to discuss SSL in depth, but if you are supporting remote users I would strongly recommend you purchase a proper signed certificate, as it will save you a lot of trouble later on.
Configuring IMAP on Exchange 2003
By default on Exchange 2003, IMAP support is installed but not enabled, so the first thing you need to do is find the service and start it. To do this, open the Services management console on your Exchange Server (Start – Run – services.msc). Scroll down to the "Microsoft Exchange IMAP4" service and double-click it to view the properties.
If you don't have the service listed, the most likely reason is that IMAP support was not installed with Exchange. In this case you will need to rerun the Exchange setup wizard and add the feature. Once you have found it, change the "Startup Type" to "Automatic", so that it will run every time the server is rebooted, and then manually start the service for the first time by clicking "Start". Once it is started you can close the window by clicking "Ok", then confirm that the MS Exchange IMAP4 service is "Started" and set to "Automatic" in the Services console before closing it. Its unlikely that you will encounter any problems at this point, but if you do, the place to start investigating is in the Event Viewer to see why the service failed to start.
Next you need to open your Exchange System Manager application, expand the "Servers" container and select your server. Drill down to the "Default IMAP4 Virtual Server" as shown on the left. Notice that the console will show you "Current Sessions", which can be helpful when checking client connectivity later on.
At this point, if you don't intend to use SSL or change any of the IMAP defaults then you've actually completed the setup and it should just work. By default all mailboxes will have IMAP access enabled (you may disable it via the "Exchange Features" tab on the user properties in the AD). However, we will make things more secure and insist that our users only connect using SSL, so right-click the IMAP4 Virtual Server and select "Properties". Change to the "Access" tab, and under Secure Communication click the "Certificate" button to open the "Web Server Certificate Wizard" – click "Next" on the welcome page.
Here we will assume that you have already installed an SSL certificate on your Exchange Server in order to secure your Outlook Web Access. If you haven't, now would be a good time to do it and come back to this afterwards. Another article on this website, "Configure SSL on OWA" explains how to do it.
The IIS Certificate wizard gives you several options at this point. You should select "Assign an existing certificate", then click Next to see the list of certificates installed on your server.
You should see something like screen shot above, although you are unlikely to have so many certificates installed on your server unless you were previously having trouble getting SSL to work. As mentioned before, it is strongly recommended that you invest in a properly signed certificate from a root provider such as Verisign or Digicert, in which case the correct certificate should be easy to identify from the "Issued By" column. See related Petri article on SSL Certificates for Exchange Server 2007/2010. Select the certificate to install by clicking on it, then click "Next" to continue the wizard. Check that the certificate details are correct on the next page, then click "Next" to confirm, and finally "Finish" the wizard to complete the installation.
You have now enabled IMAP over SSL but you are not yet requiring it on connections to your server, which we will set next. You should still be on the Access tab of the IMAP4 Virtual Server properties, so this time click the "Authentication" button under "Access Control" to open this window.
Make sure the "Requires SSL/TLS encryption" box is checked, then click Ok to return to the previous window and click the "Communication" button. In the window that opens, check the "Require secure channel" box to force all client connections to use SSL encryption.
Don't forget to make sure you've opened the required ports in your firewall (143 for IMAP, 993 for IMAP over SSL), at which point your server should be ready to accept IMAP connections. Users will just need to know the server address and the credentials for the mailbox they wish to access.
Configuring IMAP on Exchange 2007
For the sake of this guide we will assume that you have at least Service Pack 1 on your Exchange 2007 Server, as it adds the IMAP options to the Exchange Management Console. Otherwise, all IMAP configuration has to be done using the Exchange Management Shell commands.
The implementation of IMAP in Exchange 2007 has changed slightly from 2003, the main difference being that the default settings now require a secure connection. IMAP support is installed as part of the Client Access Server role (if you only have one Exchange 2007 server it will have the CAS role), but like with Exchange 2003, the IMAP4 service will be disabled. See the procedure in the previous section for how to enable it. You can access your server's IMAP settings in the EMC by expanding the Server Configuration branch and selecting "Client Access", then the "POP3 and IMAP" tab.
By default IMAP on Exchange 2007 is configured to require secure logins with SSL, and provided you already have your OWA setup to use SSL successfully, you shouldn't need to do anything else. Although it's not recommended, you may disable the SSL requirement by selecting the IMAP4 protocol as above, then clicking "Properties" in the righthand pane. Under the "Authentication" tab you can change the logon security.
As in Exchange 2003 you can also enable IMAP access on a per-mailbox level. Open the mailbox properties under Recipient Configuration – Mailbox, then select the "Mailbox Features" tab to see the option. Again, by default IMAP access is enabled for all mailboxes unless you explicitly disable it.
Sending email when using IMAP
Although technically the IMAP4 protocol can be used for sending emails as well as retrieving them (by placing them in the "Outbox" folder"), most clients do not support this, and instead expect to use SMTP for outbound email. SMTP is a tried and tested protocol which you will probably be familiar with already if you have set up a mail server before, however, there are some difficulties when using it with mobile clients. The main problem is that in order to prevent spam, relaying publicly accessible SMTP servers always restrict access, either by requiring authentication or by only allowing connections from clients on their local network. For domestic email clients, this isn't usually a problem as the ISP will allow its own users to relay email through its own SMTP server, but mobile clients may find themselves using many different ISPs in their travels.
The solution is to find a SMTP server which allows you to make an authenticated connection to it from anywhere, and then send your outbound email through it. Some ISPs include authenticated SMTP as part of their standard package, and there are also subscription services available, but there's no reason why you can't use your own Exchange Server. See related Petri article Configuring Exchange 2007 as an Authenticated or Anonymous SMTP Relay.
Conclusion
You should now have IMAP access working on your Exchange Server, and quite possibly authenticated SMTP as well, making it accessible by virtually all modern email clients. Bear in mind though that different email clients implement IMAP in subtly different ways, so it may still take a little experimentation to get them connected. I'd recommend testing with a Microsoft client like Outlook Express or Windows Mail first in order to verify your configuration before trying with third party clients. Should you then encounter problems, you can at least be pretty certain the problem is with the client and not your server, and troubleshoot accordingly.
Secure Exchange 2003 IMAP4/secure IMAP4 Publishing
http://www.isaserver.org/img/upl/exchangekit/2003secureimap4/2003secureimap4.htm
Exchange Server allows you to host a number of mail protocols that can be accessed by remote users via ISA Server 2000 Server Publishing Rules. One of these mail protocols is the Internet Mail Access Protocol version 4 (IMAP4). There are several reasons why you might want to make the IMAP4 mail access protocol your remote access mail protocol of choice:
- IMAP4 allows users to download message headers only. The message body is automatically downloaded When the user clicks on a message header. This can save a significant amount of bandwidth because users typically do not read all the new mail in their mailboxes
- IMAP4 allows users to automatically download message headers and bodies. This option can be configured on the IMAP4 client
- The user’s mail remains on the Exchange Server. Message headers and bodies are copied to the IMAP4 client, but the original messages remain on the Exchange Server. This allows the user to access the mail using another client, such as the full Outlook MAPI client, when they return to the office
- You can easily force users to use a secure connection when connecting to the IMAP4 server. The Exchange Server IMAP4 service can be configured to that the connection fails if the user tries to create a non-secure connection with the IMAP4 server.
The following procedures are discussed in this ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document:
·Enable the IMAP4 service on the Exchange Server
The IMAP4 service is disabled by default on an Exchange 2003 Server. You must enable it and configure it to start automatically. The IMAP4 service is enable by default on Exchange 2000 Server.
·Request and install a Web site certificate for the Exchange Server IMAP4 virtual server
You must bind a Web site certificate to the IMAP4 service before it can establish a secure TLS connection with the IMAP4 client. You can make either an online certificate request to an online Microsoft enterprise CA, or you can create a certificate request file and send the request to an offline CA (an enterprise CA, standalone CA or third party CA). The certificate is installed into the Exchange Server’s machine certificate store and bound to the IMAP4 service.
·Configure a secure IMAP4 virtual server
You should install and configure a secure IMAP4 virtual server. This secure IMAP4 virtual server forces the IMAP4 client to negotiate a TLS connection before user credentials are sent. If the client fails to create the secure link, the server terminates the connection attempt. This is a secure configuration because it requires the user to authenticate, the credentials are protected by TLS encryption, and the data are protected by TLS encryption.
·Create and configure an optional non-encrypted IMAP4 server
There may be circumstances when you need clients to create a non-secure connection with the Exchange Server using the IMAP4 mail protocol. In this case, you can create a second virtual IMAP4 server that allows unsecured connections but requires that the clients use integrated authentication (instead of basic) to connect. This prevents IMAP4 clients from using basic authentication. Basic authentication is insecure because the credentials are passed “in the clear”.
·Install Windows Server 2003 on the firewall computer
Windows Server 2003 is installed on the firewall computer and is used as the base operating system on which ISA Server 2000 is installed
·Install ISA Server 2000 on the firewall computer
Install ISA Server 2000 on the firewall computer after Windows Server 2003 has been installed.
·Create the IMAP4 and Secure IMAP4 Server Publishing Rules
You can create the IMAP4 and secure IMAP4 Server Publishing Rules on the ISA Server computer after the ISA Server 2000 firewall software is installed.
·SMTP Server considerations for IMAP4 and Secure IMAP4 mail clients
The IMAP4 protocol only allows the client to download message headers and bodies, similar to the POP3 protocol. Like the POP3 protocol, you need to use SMTP to send email. You can provide your own SMTP server for external users to send email to securely, or you can allow users to connect to a local SMTP server if their ISP provides one.
·Configure the mail client to support IMAP4 and Secure IMAP4 connections
The email client software must be configured to support either IMAP4 or secure IMAP4 connections with the IMAP4 server. If you require secure IMAP4, then the client must trust the CA that issued the certificate to the IMAP4 server.
Enable the IMAP4 service on the Exchange Server
The first step is to enable the IMAP4 service on the Exchange 2003 server. By default, the IMAP4 service is disabled and it is not configured to start up automatically on system startup.
Perform the following steps to enable the IMAP4 service:
- Click Start, point to Administrative Tools and click on Services (figure 1).
Figure 1
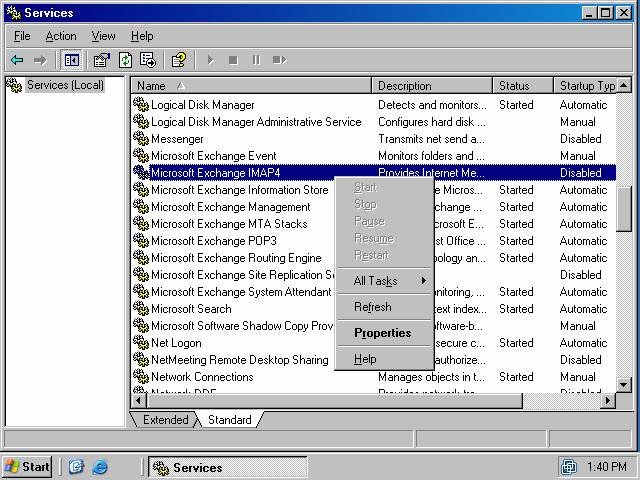
- In the Services console (figure 2), locate the Microsoft Exchange IMAP4 entry and right click on it. Click the Properties command.
Figure 2
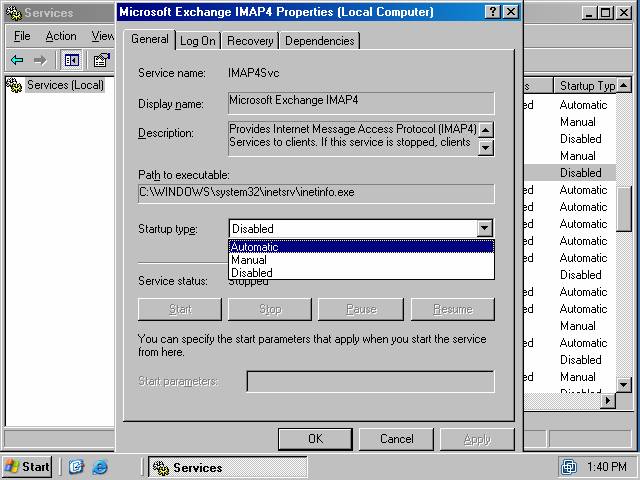
- On the Microsoft Exchange IMAP4 Properties dialog box, click the down arrow on the Startup type drop down list box (figure 3). Select the Automatic option.
Figure 3
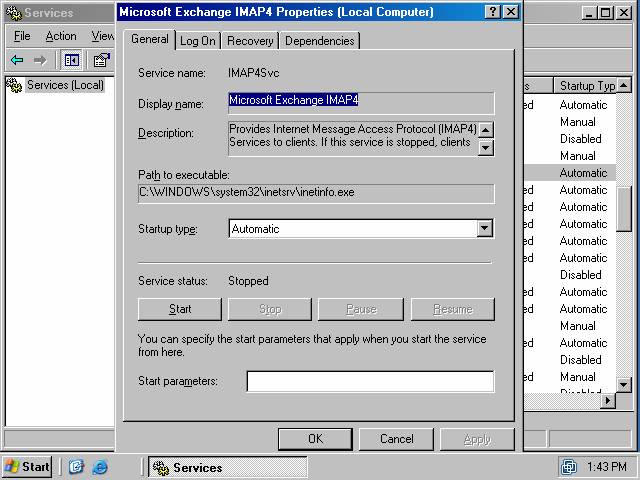
- After the Automatic option is selected, the Start button will become available (figure 4). Click the Start button to start the IMAP4 service.
Figure 4
- The Service Control dialog box shows a progress bar for starting the IMAP4 service (figure 5).
Figure 5
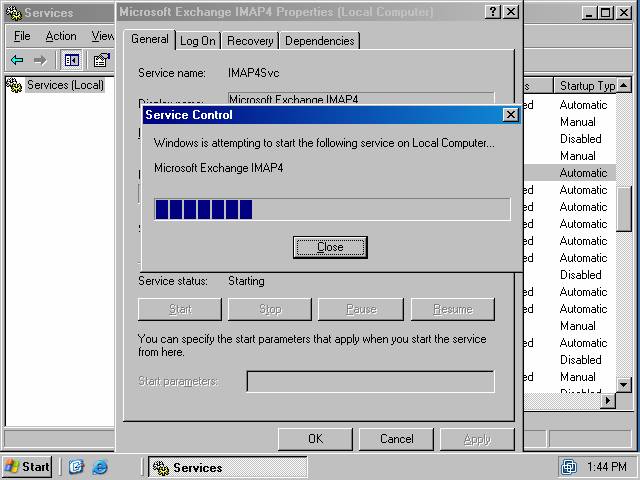
- Click OK on the Microsoft Exchange IMAP4 Properties dialog box after the service has started(figure 6).
Figure 6
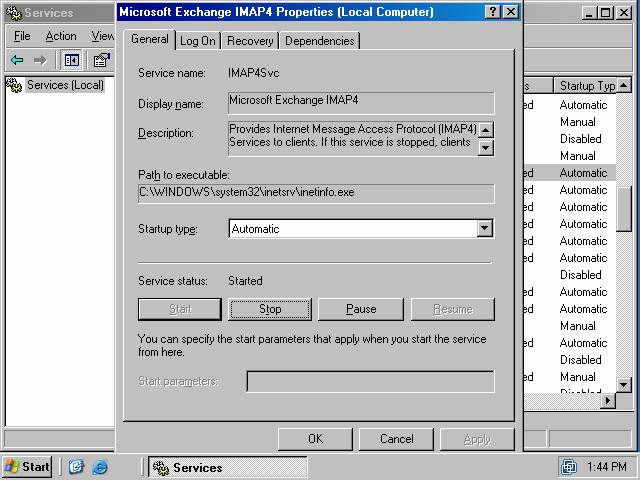
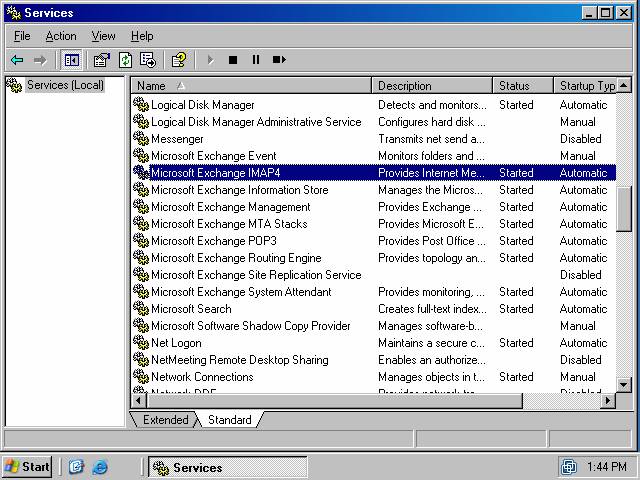
- The Microsoft Exchange IMAP4 entry in the Services dialog box will show the service as Started and the Startup Type as Automatic (figure 7).
Figure 7
Request and install a Web site certificate for the Exchange Server IMAP4 virtual server
A Web site certificate must be installed on the IMAP4 virtual server before the TLS connection can be established. ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document How to Obtain a Web Site Certificate covers the details of the Internet Information Services Web Site Certificate Request Wizard. Please refer to that ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document for details on how to obtain and install the Web site certificate on the IMAP4 virtual server.
Perform the following the following steps to begin the Web site certificate request processes for the IMAP4 server:
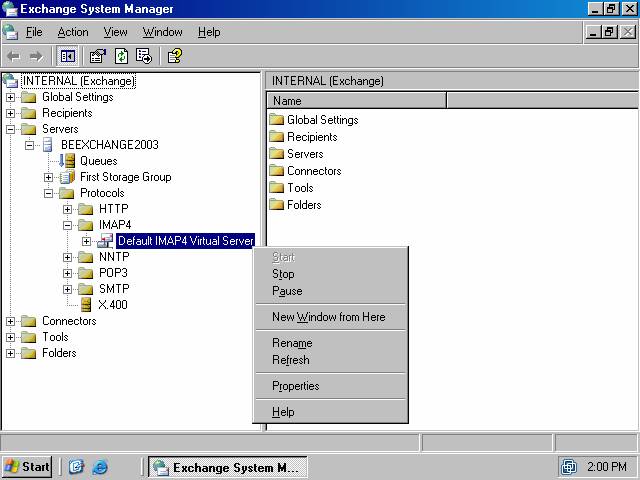
1. Open the Exchange System Manager, expand the organization name and then expand the Servers node. Expand your server name and then expand the Protocols node. Expand the IMAP4 node and click on the Default IMAP4 Virtual Server node. Right click on the Default IMAP4 Virtual Server node and click the Properties command (figure 8).
Figure 8
2. Click on the Access tab and click the Authentication button in the Access control frame (figure 9).
Figure 9
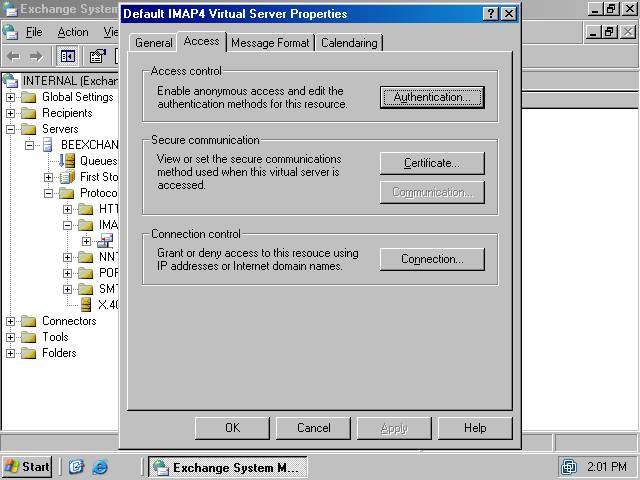
3. Read the information on the Welcome to the Web Server Certificate Wizard page and click Next (figure 10). Follow the onscreen instructions provided by the Wizard to complete the request. For a detailed account of how to request and install the Web site certificate, please refer to ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document How to Obtain a Web Site Certificate.
Figure 10
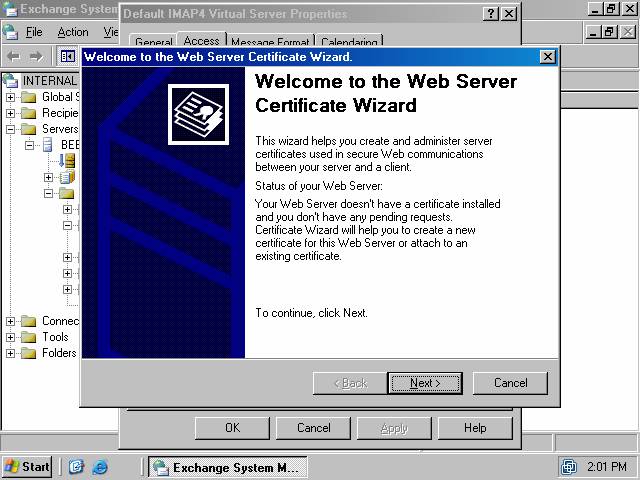
4. The Communication button in the Securecommunication frame becomes available after the certificate is installed (figure 11). You will use this button later to force TLS security on IMAP4 connections with this IMAP4 server
Figure 11
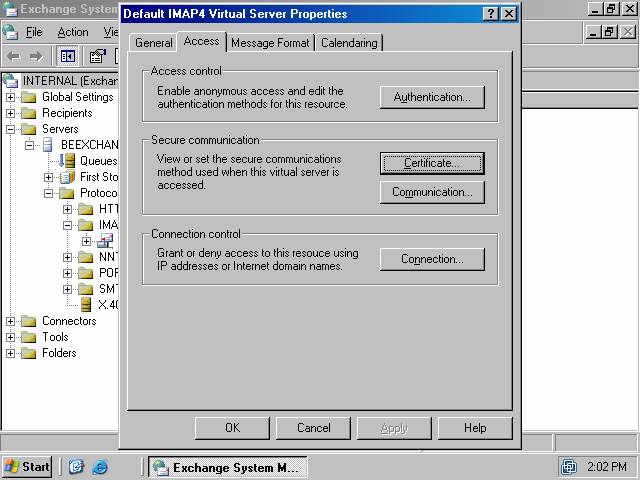
The IMAP4 virtual server will be able to create secure connections using TLS security after the certificate is installed.
Configure the Secure IMAP4 virtual server
You can configure the IMAP4 virtual server now that the IMAP4 virtual server has a certificate installed:
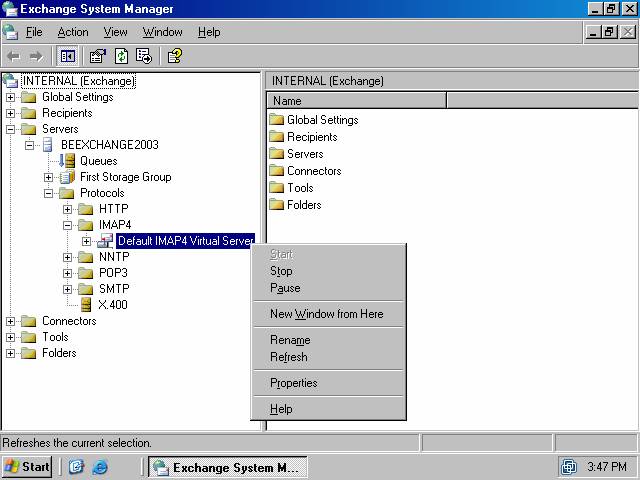
1. Open the Exchange System Manager, expand your organization name and expand the servers node. Expand your server name and then expand the Protocols node. Expand the IMAP4 node and click on the Default IMAP4 Virtual Server node. Right click on the Default IMAP4 Virtual Server node and click the Properties command (figure 12).
Figure 12
2. The General tab is the first to appear in the Default IMAP4 Virtual Server Properties dialog box (figure 13). Click the down arrow for the IP address drop down list and select an IP address for the secure IMAP4 site. Make sure that this is not the same IP address used by any other IMAP4 server on the Exchange Server computer. You can use the same IP address that is being used by another Exchange Server service, such as the POP3 service, but do not assign the same address to two IMAP4 virtual servers.
Figure 13
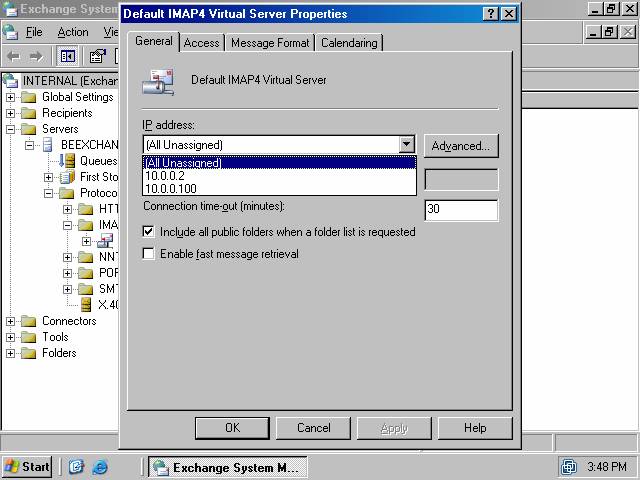
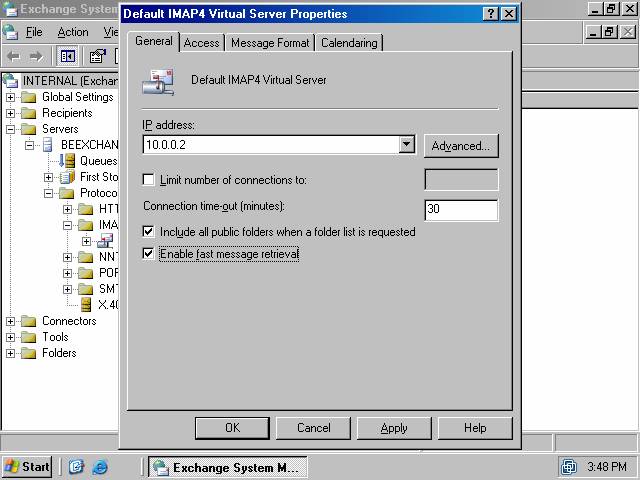
3. Select the Enable fast message retrieval option on the General tab. This will significantly improve the performance of the IMAP4 client when it retrieves messages from the Exchange Server’s IMAP4 service (figure 14). Almost all IMAP4 clients support fast message retrieval, including all versions of Outlook Express. Click Apply.
Figure 14
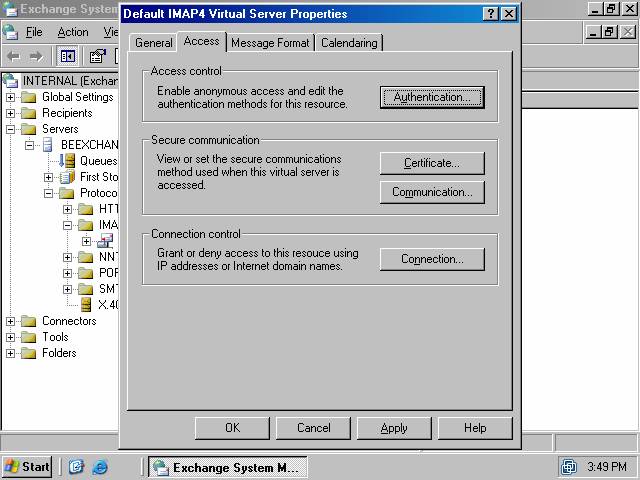
4. Click on the Access tab. Click the Authentication button in the Access control frame (figure 15).
Figure 15
5. You can select the forms of authentication you want to support in the Authentication dialog box (figure 16). You have the following options:
Basic authentication (password is send in clear text)
The basic authentication option insures the highest level of compatibility with different IMAP4 clients. However, basic authentication passes user name and password information “in the clear”. You should use basic authentication only when you protect the connection using TLS encryption.
Requires SSL/TLS encryption
This setting forces the IMAP4 client to establish an SSL/TLS connection before credentials are sent to the IMAP4 server. If the client does not successfully establish a secure connection with the IMAP4 server, then the connection is dropped without the exchange of credentials.
Simple Authentication and Security Layer
Use this option to allow the IMAP4 client to use integrated authentication (NTLM).
We recommend that you enable all options. This allows the greatest level of flexibility and security for your IMAP4 client/server connections.
Figure 16

6. Click on the Communication button in the Securecommunication frame (figure 17).
Figure 17

7. Put a checkmark in the both the Requiresecure channel and Require 128-bit encryption checkboxes (figure 18). This option forces the IMAP4 client to negotiate a secure TLS connection before any credentials or data is transferred between the IMAP4 client and server. Click OK.
Figure 18

8. Click on the Calendaring tab (figure 19). The settings on this tab determine the URL IMAP4 clients receive when the download meeting requests. Note that you should use SSL when connecting to the Outlook Web Access (OWA) server. Select the Use fron-end server option and type in the fully qualified domain name (FQDN) of the OWA server. This FQDN must be resolvable to an address that remote IMAP4 clients can reach. Place a checkmark in the Use SSL connections checkbox to force the IMAP4 client to use SSL to connection to the OWA site.
Figure 19

Create and Configure an Optional Non-Encrypted IMAP4 Server
I strongly encourage you to use only secure connections when connecting to the IMAP4 server. The only way to insure all connections with the IMAP4 server are secure is to force TLS security at the IMAP4 server. When the secure connection is enforced, IMAP4 clients that do not, or can not, establish a TLS link will not be able to connect.
There may be circumstances when you want to allow non-secure connections to the IMAP4 server. You should create a second virtual IMAP4 server if you require non-secure IMAP4 connections. This allows you to force security on the first IMAP4 virtual server and allow non-secure connections to the second IMAP4 virtual server.
Note:
You will need additional IP addresses bound to the Exchange Server’s network interface card if you have more than one virtual IMAP4 server on the Exchange Server. Each virtual server requires its own IP address.
Perform the following steps to create a second virtual IMAP4 server that accepts non-secure connections:
1. Right click on the IMAP4 node in the left pane of the Exchange System Manager console, point to New and click on IMAP4 Virtual Server (figure 20).
Figure 20

2. Type in a name for the virtual IMAP4 server in the Name text box on the Welcome to the New IMAP4 Virtual Server Wizard page (figure 21). Click Next.
Figure 21

3. Click the down arrow on the Select the IP address for this IMAP4 virtual server drop down list box on the Select IP Address page (figure 22). Select an IP address that is not being used by any other virtual IMAP4 server on the Exchange Server machine. Click Finish.
Figure 22

4. The new virtual IMAP4 server appears in the Exchange System Manager (figure 23).
Figure 23

5. Right click on the new virtual IMAP4 server name in the left pane of the console and click the Properties command. On the General tab of the virtual IMAP4 server’s Properties dialog box, put a checkmark in the Enable fast message retrieval checkbox (figure 24). Click Apply.
Figure 24

6. Click on the Access tab (figure 25). Click the Authentication button in the Access control frame.
Figure 25

7. On the Authentication dialog box (figure 26), remove the checkmark from the Basic authentication (password is sent in clear text) checkbox. You do not want to allow basic authentication against this virtual IMAP4 server because the user name and password will not be protected by TLS encryption. Place a checkmark in the Simple Authentication and Security Layer checkbox. NTLM authentication is much more secure than basic authentication, although it is less secure when not protected by TLS encryption.
Figure 26

8. Click on the Calendaring tab (figure 27). The settings on this tab determine the URL IMAP4 clients receive when the download meeting requests. Note that you should use SSL when connecting to the Outlook Web Access (OWA) server. Select the Use fron-end server option and type in the fully qualified domain name (FQDN) of the OWA server. This FQDN must be resolvable to an address that remote IMAP4 clients can reach. Place a checkmark in the Use SSL connections checkbox to force the IMAP4 client to use SSL to connection to the OWA site.
Figure 27

The virtual IMAP4 servers are now configured and ready to accept incoming IMAP4 and secure IMAP4 connections.
Installing Windows Server 2003 on the Firewall Computer
The computer that will be the ISA Server 2000 firewall should meet the following minimum requirements:
- A personal computer with a 1.5 MHz or higher Intel/AMD-compatible CPU
- For the operating system, Windows 2000 Service Pack 4 or Windows Server 2003
- 256 MB of memory (RAM)
- 20 MB of available hard disk space for program files
- Two network adapters that is compatible with Windows 2000 or Windows Server 2003 , for communication with the internal and external networks
- One local hard disk partition that is formatted with the NTFS file system for log files and Web caching (if you wish to run the ISA Server firewall’s Web caching facilities)
The ISA Server firewall and Web caching components work very well on modest hardware. This is true even when the SMTP filter is enabled and protecting the published SMTP servers. However, if you run decide to use the SMTP Message Screener on the firewall, or if you use SSL to protect Web Published Web site, or if you use the ISA Server firewall as a VPN server, you need to increase the minimum requirements to support encryption services.
Install ISA Server 2000 on the Firewall Computer
Install ISA Server 2000 after installing Windows Server 2003 onto the firewall computers. You must go through some specific procedures outside of the standard ISA Server 2000 installation when installing the firewall software onto a Windows Server 2003 computer. Please refer to ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document Installing ISA Server 2000 on Windows Server 2003.
Create the IMAP4 and Secure IMAP4 Server Publishing Rules
Now you can create the IMAP4 and secure IMAP4 Server Publishing Rules. Perform the following steps to create the IMAP4 Server Publishing Rule:
1. Open the ISA Management console, expand the Servers and Arrays node and then expand the server name. Expand the Publishing node and click on the Server Publishing Rules node. Right click on the Server Publishing Rules node, point to New and click on Rule (figure 28).
Figure 28

2. Type in a name for the Server Publishing Rule in the Server publishing rule name text box on the Welcome to the New Server Publishing Rule Wizard page (figure 29). Click Next.
Figure 29

3. On the Address Mapping page (figure 30), type in an IP address for the internal secure virtual IMAP4 server in the IP address of internal server text box. Click the Browse button next to the External IP address on ISA Server text box. Select the IP address on the external interface of the ISA Server firewall that you want to listen for incoming secure IMAP4 connection requests in the New Server Publishing Rule Wizard dialog box. Click OK.
Figure 30

4. Click Next on the Address Mapping page (figure 31).
Figure 31

5. Click the down arrow for the Apply the rule to this protocol drop down list box on the Protocol Settings page (figure 32). Select the IMAP4 Server.
Figure 32

6. On the Client Type page, select the Anyrequest option (figure 33). Click Next.
Figure 33

7. Review your settings on the Complete the New Server Publishing Rule Wizard page and click Finish (figure 34).
Figure 34

8. The new IMAP4 Server Publishing Rule appears in the right pane of the ISA Management console (figure 35).
Figure 35

Perform the following steps to create the secure IMAP4 Server Publishing Rule:
1. Type in a name for the Server Publishing Rule in the Server publishing rule name text box on the Welcome to the New Server Publishing Rule Wizard page (figure 36). Click Next.
Figure 36

2. On the Address Mapping page (figure 37), type in an IP address for the internal secure virtual IMAP4 server in the IP address of internal server text box. Click the Browse button next to the External IP address on ISA Server text box. Select the IP address on the external interface of the ISA Server firewall that you want to listen for incoming secure IMAP4 connection requests in the New Server Publishing Rule Wizard dialog box. Click OK.
Figure 37

3. Click Next on the Address Mapping page (figure 38).
Figure 38

4. Click the down arrow for the Apply the rule to this protocol drop down list box on the Protocol Settings page (figure 39). Select the IMAPSServer.
Figure 39

5. On the Client Type page, select the Anyrequest option (figure 40). Click Next.
Figure 40

6. Review your settings on the Complete the New Server Publishing Rule Wizard page and click Finish (figure 41).
Figure 41

7. The new IMAP4 Server Publishing Rule appears in the right pane of the ISA Management console (figure 42).
Figure 42

SMTP Server considerations for IMAP4 and Secure IMAP4 mail clients
The IMAP4 client receives message headers and message bodies from the IMAP4 server. The default behavior of the Outlook Express IMAP4 client is to download the message header only and download the message body after the user clicks on the message header. You can configure most IMAP4 clients to automatically download the message header and body. The message stays on the Exchange Server and is available to the user at a later time. For example, the user might use IMAP4 while on the road and the full MAPI Outlook client while in the office.
IMAP4 allows for downloading only. You must use SMTP to send responses to the messages or to create and send new mail. The IMAP4 client has several options:
- Use the SMTP server provided by the ISP
If the IMAP4 user logs onto an ISP that provides an SMTP server address, the user can use the local ISP’s SMTP server to send messages. The ISP may even offer secure SMTP access that allows the use to protect credentials and data using SSL/TLS. Note that when the user uses a local ISP’s SMTP server, it becomes the users’ responsible to force a secure connection with the SMTP server.
- Use an SMTP server you provide for the IMAP4 user
If the user does not log on to a local ISP, or uses an ISP that does not provide a secure SMTP server, you can create your own secure SMTP server for your users. The secure SMTP server can be placed on the ISA Server firewall as a secure SMTP relay, or you can publish a secure SMTP virtual server located on the Exchange Server.
Please refer to ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document Configuring a Windows Server 2003-based ISA Server as a Secure Authenticating SMTP Relay for information on how to configure a secure authenticating SMTP server on the ISA Server firewall.
Please refer to ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document Secure Exchange 2003 SMTP/SMTPS publishing for information on how to configure a secure authenticating SMTP server on the ISA Server firewall.
- Provide no publicly accessible SMTP mail facility and require the user to use a secure VPN connection to send mail
Another option is to allow the user to connect to a secure IMAP4 server over the Internet, but require that all outbound messages be sent over a VPN link. This configuration is problematic because the IMAP4 client is configured to a public address to connect to the secure IMAP4 server, but is configured to use the Exchange Server’s private address that it can connect to after the VPN connection is established. The problem is that this configuration will not allow the IMAP4 component to work when the VPN connection is established because that would require split tunneling and split tunneling is an extreme security risk. The most common solution to this problem is to have the user change the IP address used for the IMAP4 server to the Exchange Server’s internal IP address while connected to the VPN and then change it back to the public address used in the secure IMAP4 Server Publishing Rule when the VPN link is disconnected.
We recommend that you create your own secure SMTP server on either the ISA Server firewall computer, or on the Exchange Server itself. This option allows you to easily force the client to use a secure connection when connecting to the SMTP server. If the user removes the secure configuration on the client, no SMTP mail will be sent.
Configuring the SMTP Client to use TLS Encryption for SMTP Messages
The SMTP client must be configured to negotiate a TLS connection with the authenticating SMTP relay. The method used to configure the client to use secure SMTP connections varies with the client. The following ISA Server 2000 Exchange Server 2000/2003 Deployment Kit documents discuss how to configure some popular SMTP client to the SMTP relay using TLS:
- Configuring Outlook Express
- Configuring Outlook 2000
- Configuring Outlook 2002
- Configuring Outlook 2003
Regardless of the SMTP email client application, all clients will need a copy of the Root CA certificate of the CA that assigned the authenticating SMTP server its Web site certificate. Please refer to ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document How to Import the Root CA Certificate into Email Client Certificate Stores
Summary
In this ISA Server 2000 Exchange Server 2000/2003 Deployment Kit document we discussed the procedures required to create both a secure IMAP4 and a non-secured IMAP4 server. You saw how to request a certificate for the IMAP4 server and how to force a secure connection to the server. You also learned how to create a second virtual IMAP4 server that allows non-secured IMAP4 connections for those clients that are unable to create secured connections. SMTP server issues were discussed and several alternatives presented.
